Hyperautomation adoption
Cloud Security and Operational excellence

ABSTRACT
In an era where digital transformation is paramount, hyperautomation emerges as a critical catalyst, especially within the realms of cloud and security operations. This white paper delves into the concept of hyperautomation, propelled by advanced technologies such as Generative AI with Robotic Process Automation related to Cloud and security operations for AIOps to automate processes beyond traditional capabilities. Guided by Gartner's insights and predictions, we explore how hyperautomation acts as an indispensable enabler for enhancing security, operational efficiency, and cost optimization in cloud environments. Through autobotAI’s innovative platform, we illustrate the practical application and transformative potential of hyperautomation, underscoring its significance in navigating the complexities of today's digital landscape.

INTRODUCTION
The rapid acceleration of digital initiatives across various industries has underscored the critical need for advanced automation solutions. These solutions are pivotal in navigating the complex challenges associated with cloud operations and security. Hyperautomation stands at the confluence of multiple technological evolutions, aiming to automate the complex decision-making and processes that standard automation tools could not address. This comprehensive approach is designed to not only augment human capabilities but also to foster a more resilient, efficient, and secure digital ecosystem. Within this evolving context, autobotAI distinguishes itself as a key player. It embodies the essence of hyperautomation, streamlining cloud operations, bolstering security measures, and driving significant cost efficiencies.
As organizations set their sights on adopting hyperautomation, it becomes imperative to outline a clear execution plan. Identifying labor-intensive or repeatable processes that will benefit managed security service providers (MSSPs), Cloud detection and response (CDR) providers, and large enterprises is crucial. This approach ensures an immediate return on investment (ROI) by eliminating the administrative overhead associated with incident response, IAM, Threat hunting, CSPM based operation. With a strategic direction in place, Adoption Leaders can then establish evaluation criteria that include key operational metrics such as mean time to respond / remediate (MTTR), or service level objectives (SLOs), alongside business metrics like profit margins. It's essential to recognize that the metrics driving the desired outcomes may extend beyond the specific areas being automated.
The successful implementation, monitoring, and assessment of hyperautomation initiatives necessitate the involvement of Adopting Teams. Comprising security experts and users, these teams are instrumental in mitigating implementation challenges and enhancing the likelihood of achieving the set goals, thereby playing a critical role in the seamless integration and effective utilization of hyperautomation within organizational frameworks.
Cybersecurity Agent Builders
autobotAI as a Platform
Build, deploy, and manage intelligent security agents that automate response and remediation workflows
autobotAI
Leading the Future of Security Automation
Gartner Impact Radar
- Enhancements in analytics and automatic remediation capabilities will redirect 30% of IT operations efforts from support to continuous engineering through 2024.
- By 2024, 40% of product and platform teams will employ AIOps for automated change risk analysis in DevOps pipelines, minimizing unplanned downtime by 20%.
- Over 75% of large enterprises in mature economies will adopt container management by 2024, driven by the increasing adoption of cloud-native applications and infrastructure.
- By 2025, 50% of enterprises will have implemented AI orchestration platforms to operationalize AI, a significant increase from less than 10% in 2020.
Agentic Workflow
While hyperautomation forms the foundation of autobotAI, Generative AI plays a crucial role in augmenting our platform's capabilities, particularly in the realm of security response and remediation. It's important to understand that while many tools leverage AI for Detection Engineering, autobotAI focuses on the critical next step: automating and optimising the actions required to respond to and remediate security incidents and operational issues.
At the heart of autobotAI's approach to automation lies the concept of agentic workflows. These are structured, deterministic sequences of tasks designed to achieve specific outcomes, such as patching a vulnerability, remediating a misconfiguration or responding to threat.
Generative AI, particularly Large Language Models (LLMs), enhances these workflows in several key ways:
- Intelligent Analysis and Contextual Understanding: LLMs can analyse alerts and data from various security and cloud tools integrated with autobotAI. This enables the platform to gain a deeper understanding of the context surrounding an event, going beyond simple pattern matching. For example, an LLM can process the details of an alert, correlate it with threat intelligence and with resource tag, resource owner details it can identify the most appropriate remediation steps based on the specific environment.
- Dynamic Workflow Customisation: While agentic workflows are primarily deterministic, generative AI can introduce a degree of flexibility. Based on the analysis of an event, the LLM can dynamically select or adjust specific steps within a predefined workflow to ensure the most effective response.
- Enhanced Human Interaction: In many critical scenarios, autobotAI incorporates human review and approval steps within its agentic workflows. Generative AI can assist in preparing clear and concise summaries of the incident and the proposed remediation actions with clickable buttons to proceed or archive security finding, making it easier and faster for security teams to understand the situation and make informed decisions. This ensures that human expertise remains central to critical operational changes.
- AI Agents within Agentic Workflows: While autobotAI primarily leverages agentic workflows for reliable and repeatable outcomes, individual steps within these workflows can be powered by AI agents + Deterministic nodes. These AI agents possess a degree of autonomy to perform specific tasks, such as gathering additional information from various sources to enrich the context of an incident. For example, an AI agent could be tasked with fixing container image vulnerability can generate fixed version of Manifist file by collecting data from vulnerability scanners and open-source packages. And instead of stopping at suggestion Agentic workflow can actually create branch and PR in code repository with fixed version of code (for developer review).
Security Automation use cases
Identity and access management (IAM) automation
The IAM-based automation use cases focus on streamlining identity lifecycle processes, such as efficient onboarding/offboarding, strict contractor management, and disabling inactive accounts. They also aim to strengthen IAM posture through auditing, Just-in-Time access, and automated investigation of anomalies, alongside improving response to service requests by optimizing access approvals, simplifying self-registration , and automating permission elevation, thereby enhancing the user experience for information employees.
CSPM, KSPM, DSPM automation
Use cases to automate remediation findings from CSPM, KSPM, and DSPM tools leverage advanced algorithms triggering context-aware remediation workflows. For critical production environments, the system escalates issues with urgent notifications requiring human approval, ensuring that changes are reviewed thoroughly to mitigate risks. This approach ensures that security postures are strengthened across all deployment stages, with human oversight preserved for critical decisions, thereby optimizing the balance between speed and security.
Threat intel integrated Incident response automations
Threat intelligence-integrated incident response automation streamlines the handling of security events and alerts by correlating, enriching, and prioritizing incoming data from various sources. By integrating threat intelligence (TI) feeds, the system enhances event context, automates containment, investigation, and remediation actions, and efficiently manages block lists. Additionally, it facilitates communication and coordination with IT, developers, and business owners for comprehensive incident management. This automation not only accelerates response times but also ensures that security measures are dynamically updated based on the latest threat intelligence, significantly improving the efficiency and effectiveness of SOC operations.
Availability based operations automation
Availability-based operations automation streamlines the process of ensuring continuous application uptime by automatically triggering a set of troubleshooting protocols upon detection of downtime. Utilizing monitoring tools for initial detection, the automated workflow promptly checks for issues such as log storage constraints and service disruptions. It then executes predefined standard operating procedures to address these problems, such as service restarts or resource reallocation. This automation significantly lightens the load on CloudOps and SecOps teams by swiftly identifying, remedying, and verifying the resolution of performance, scalability, or business impact issues, ensuring minimal downtime and maintaining operational continuity.
Hyperautomation in security has reached a critical mass. The Gartner report considers it an enterprise investment that will have the most long-term impact and ROI. autobotAI is designed to help CloudOps and SecOps teams do task and process mining and help teams to automate security and cloud operations across platforms like AWS, Azure, GCP, and Kubernetes is critical step to scale operations with small technical expert teams. autobotAI stands out by integrating Customer's own generative AI with workspace based architecture support to provide complete data and permission sovereignty, facilitating more intuitive and context-aware automation workflows.
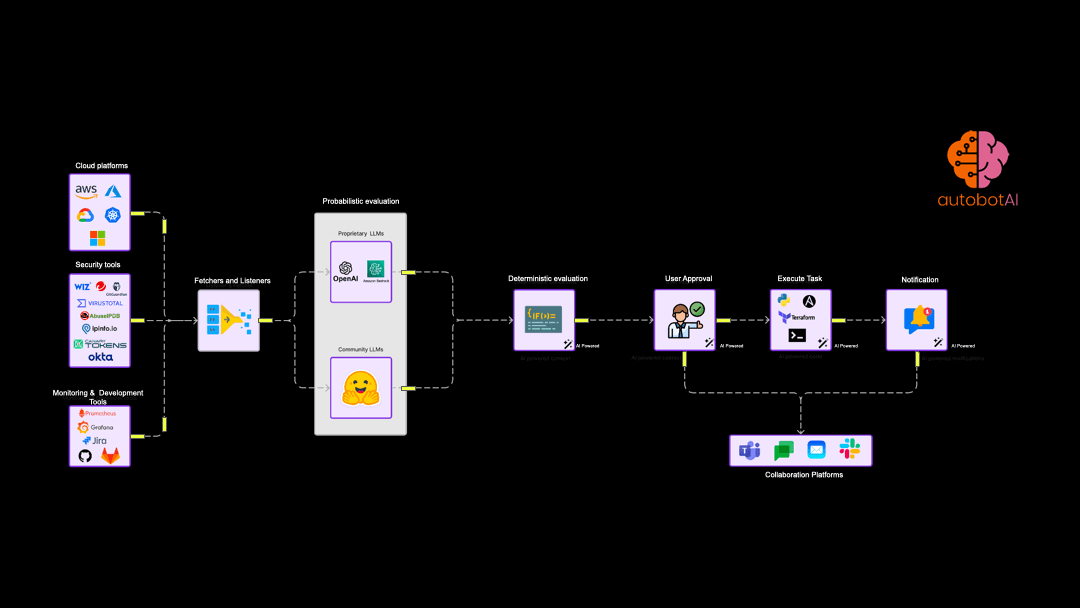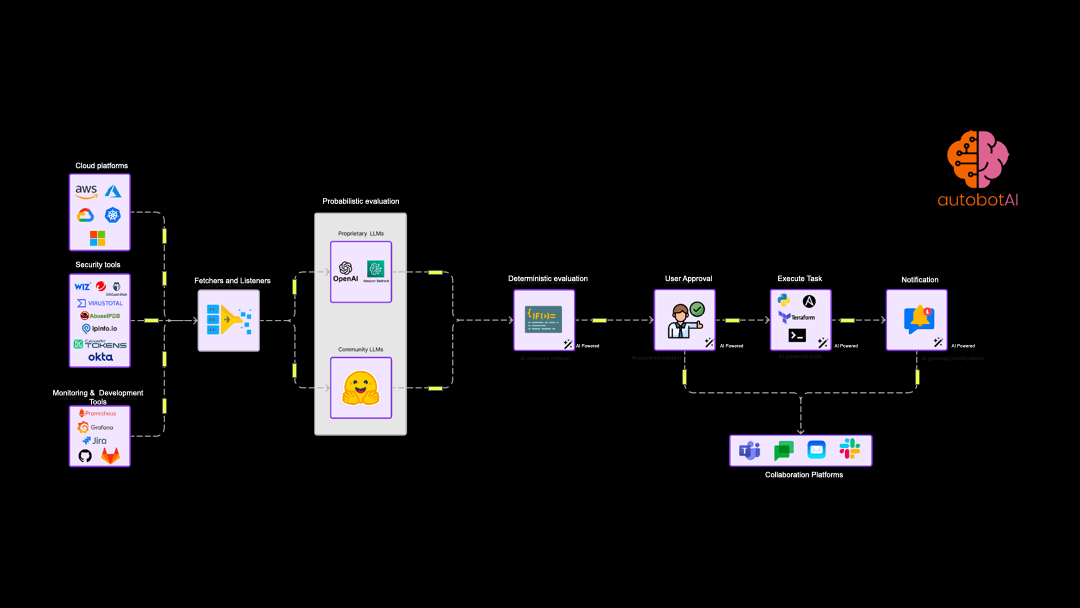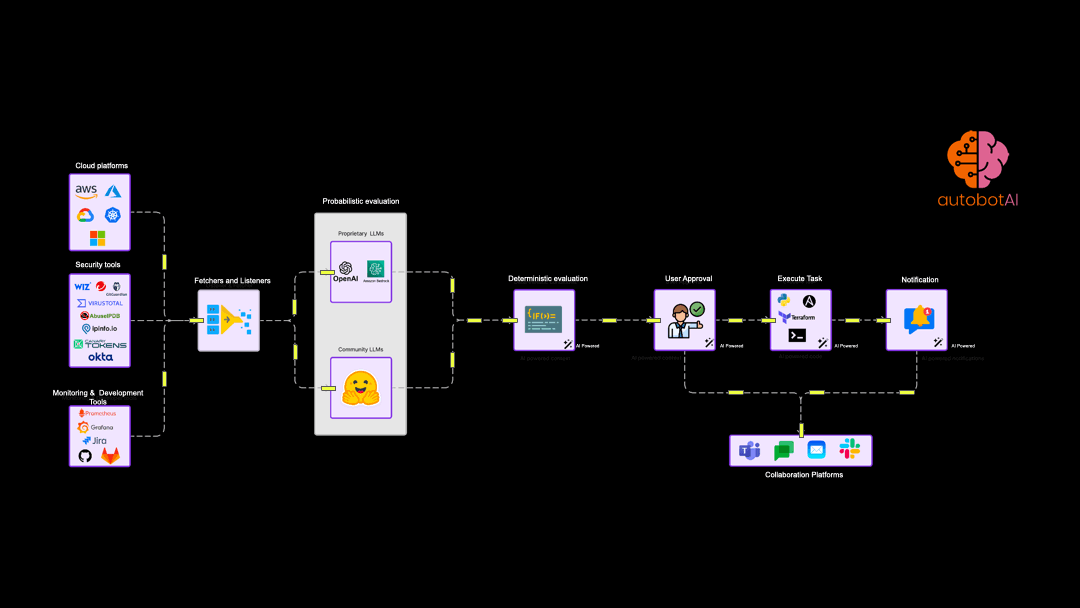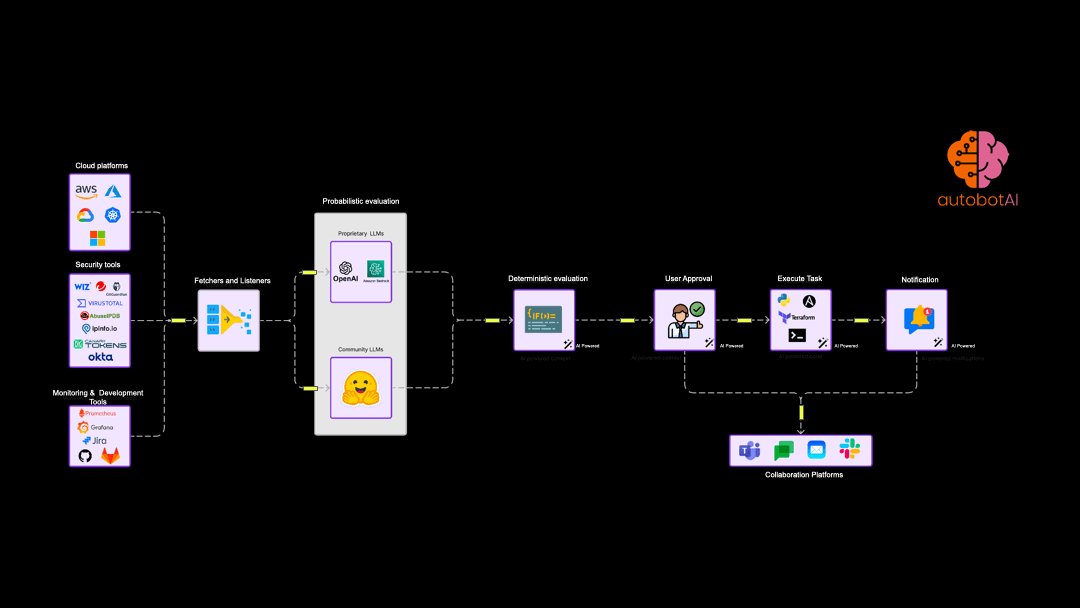
Example automation use cases
Just in time access
automation use case that provide self-service portal to users to trigger request based elevated access controls
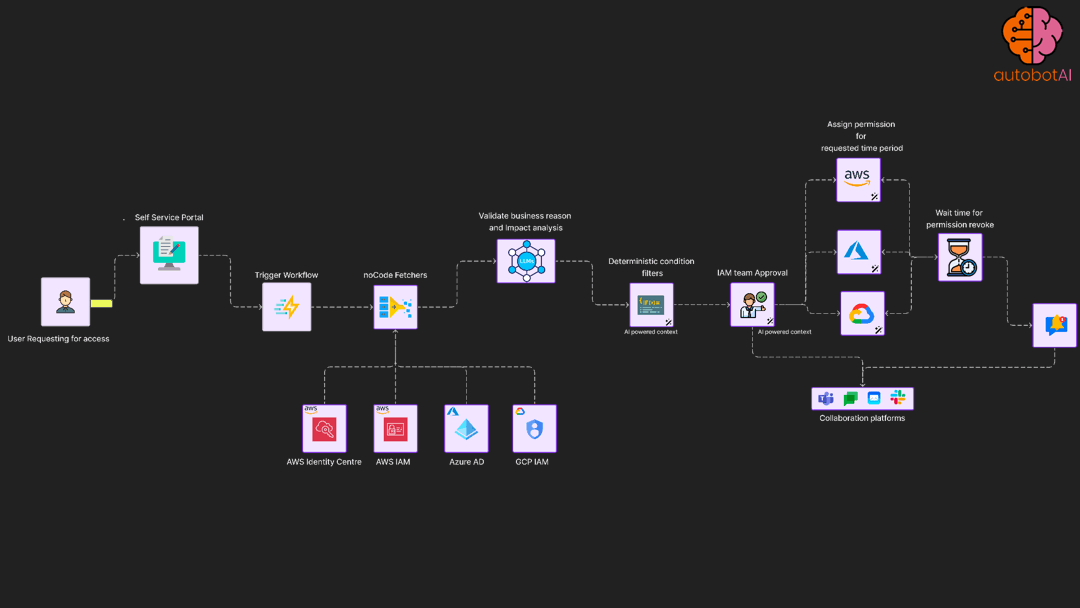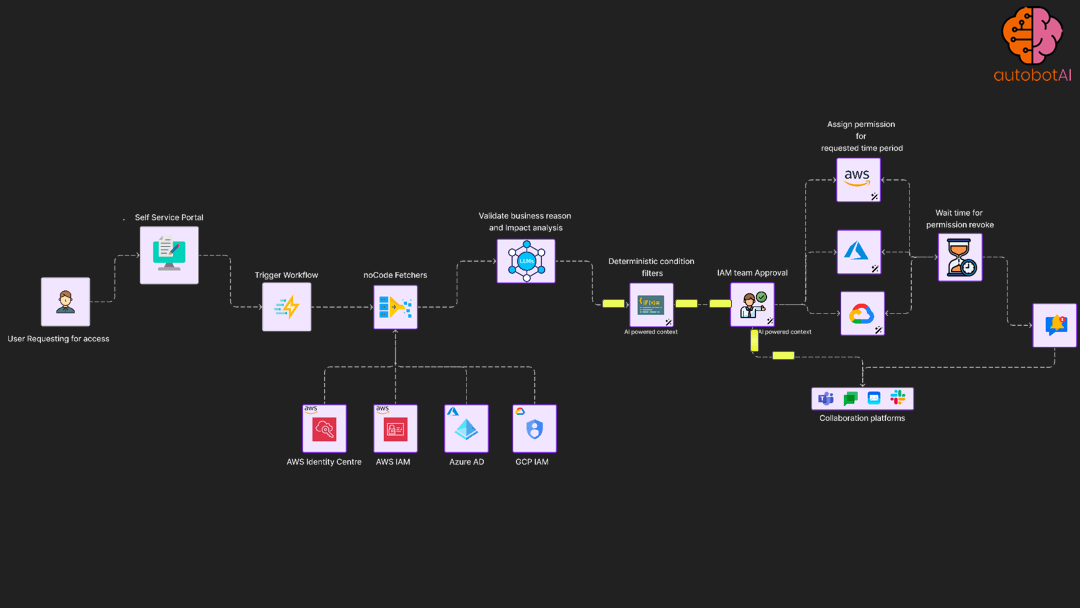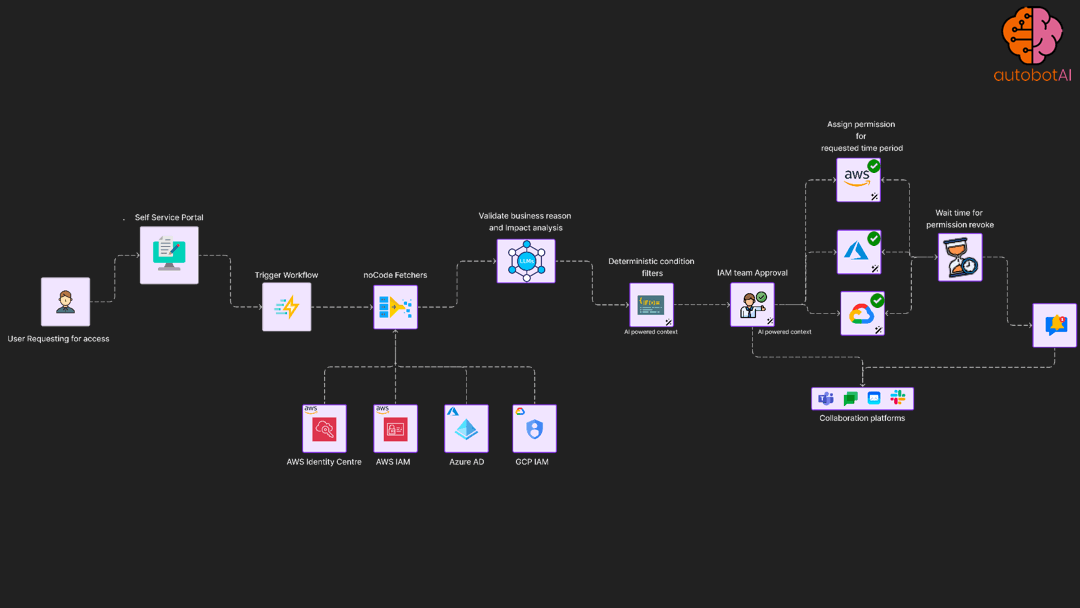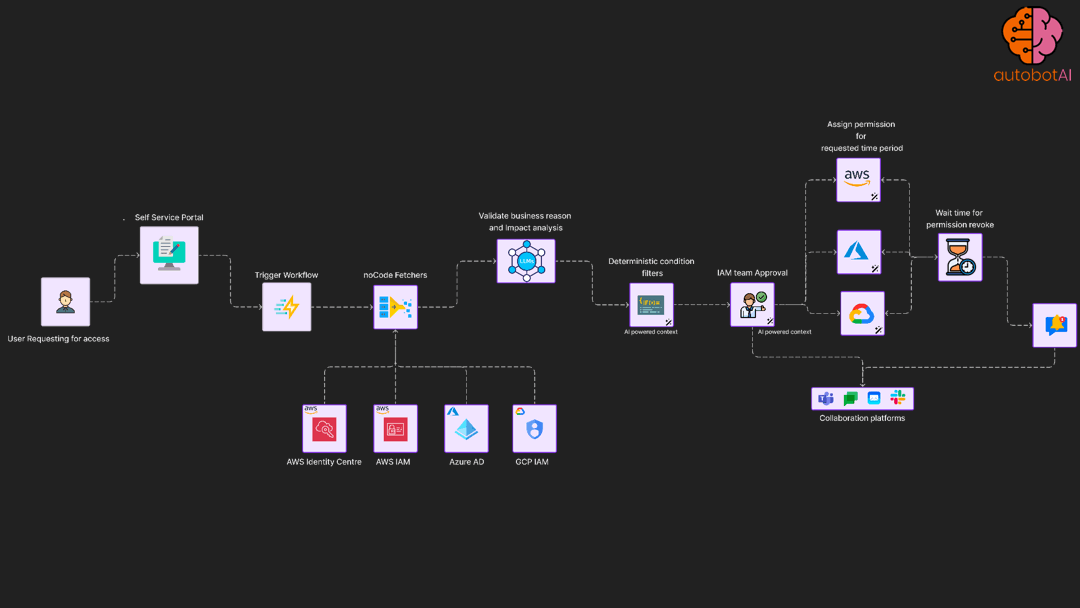
Least privilege enforcement automation
Periodically access permission utilisation for roles and apply permission boundary
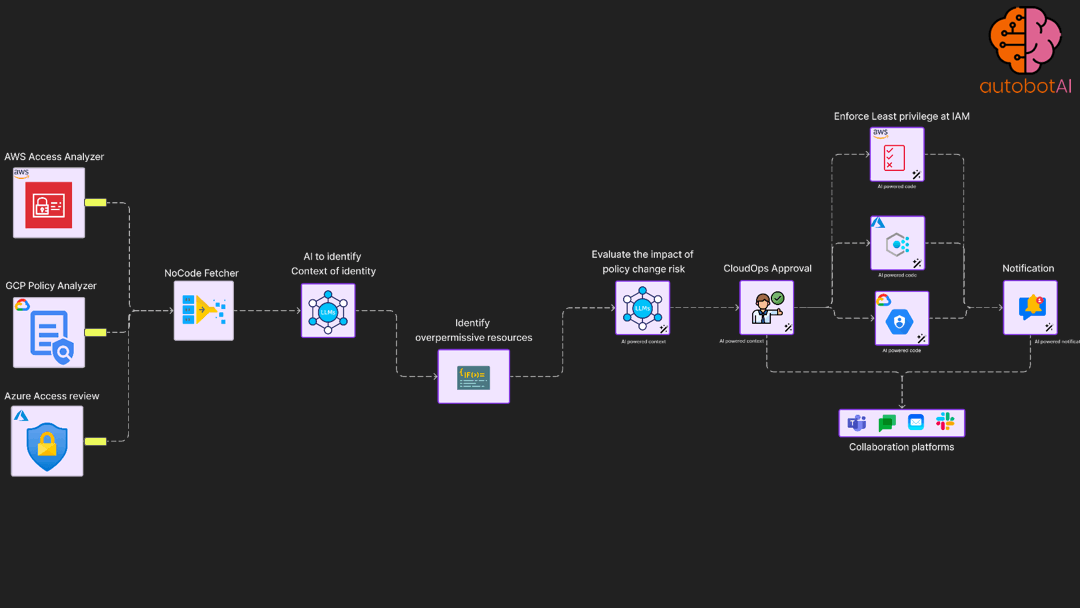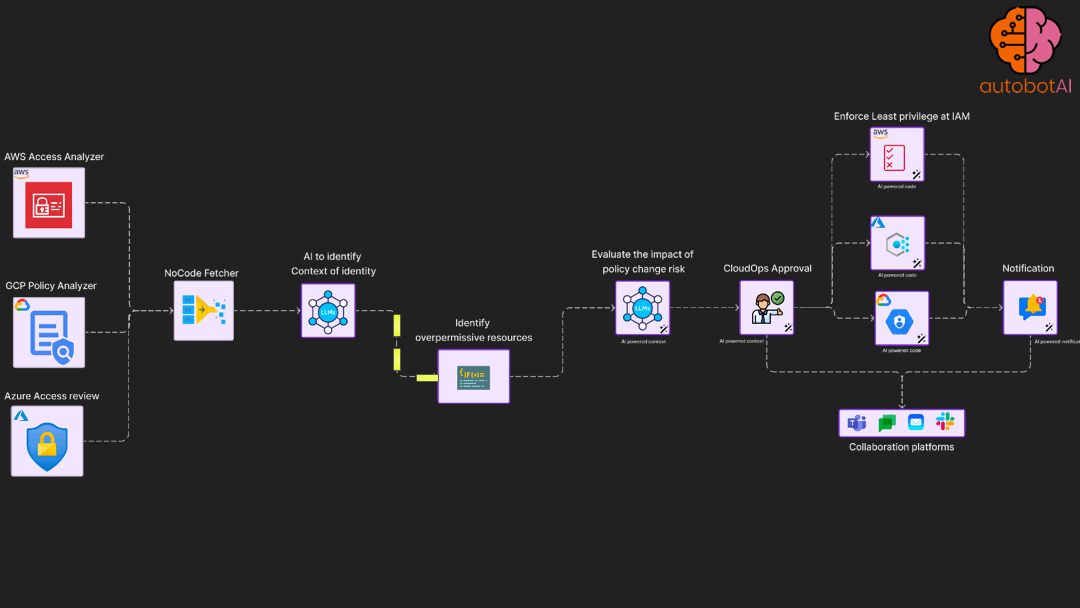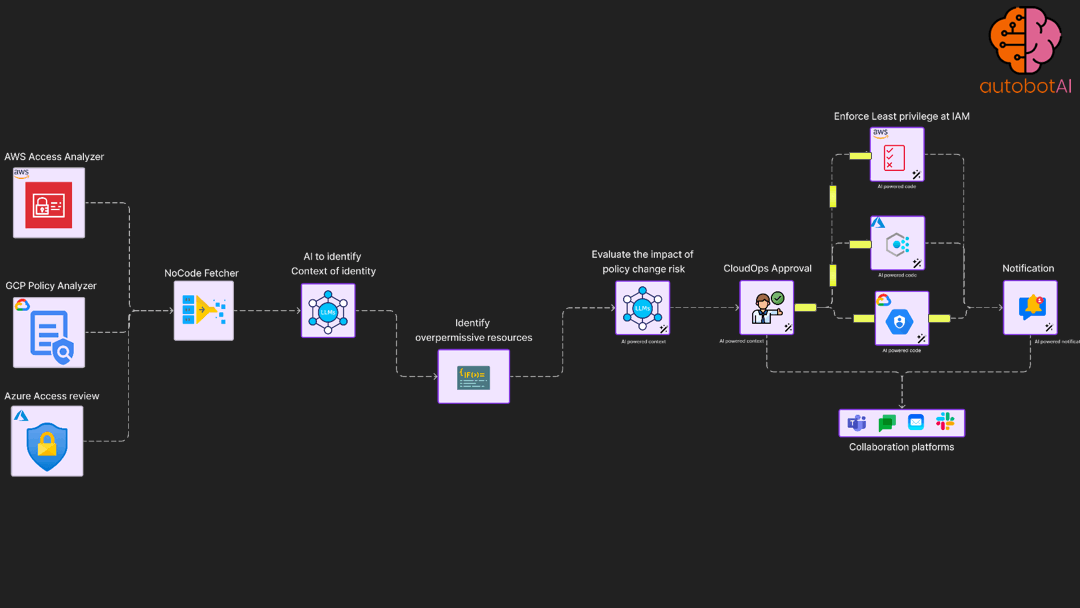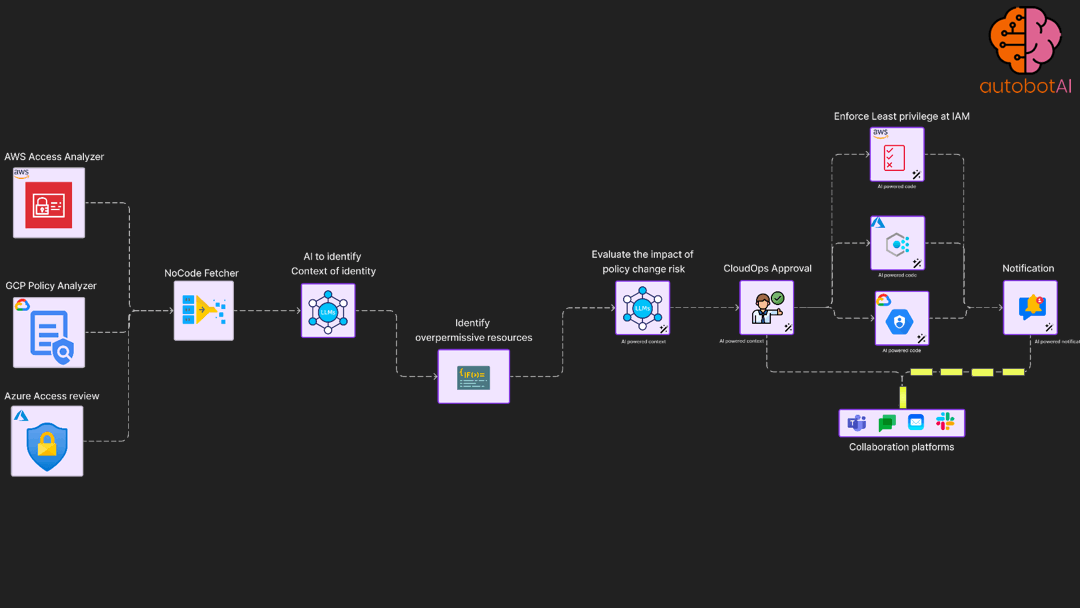
Incident response
Incident response with Cloud native and partner's security services integration.
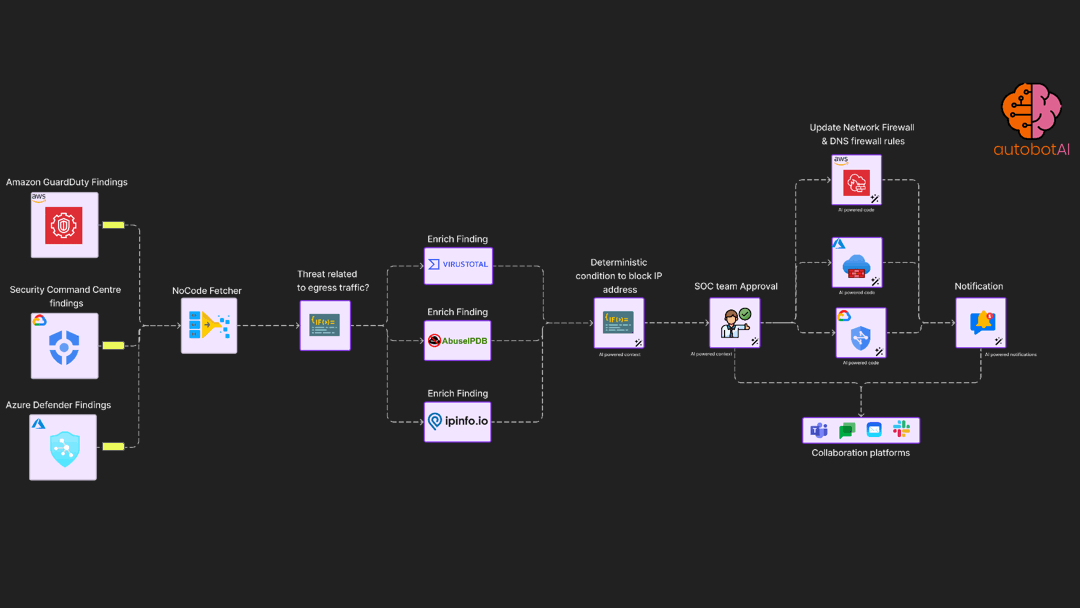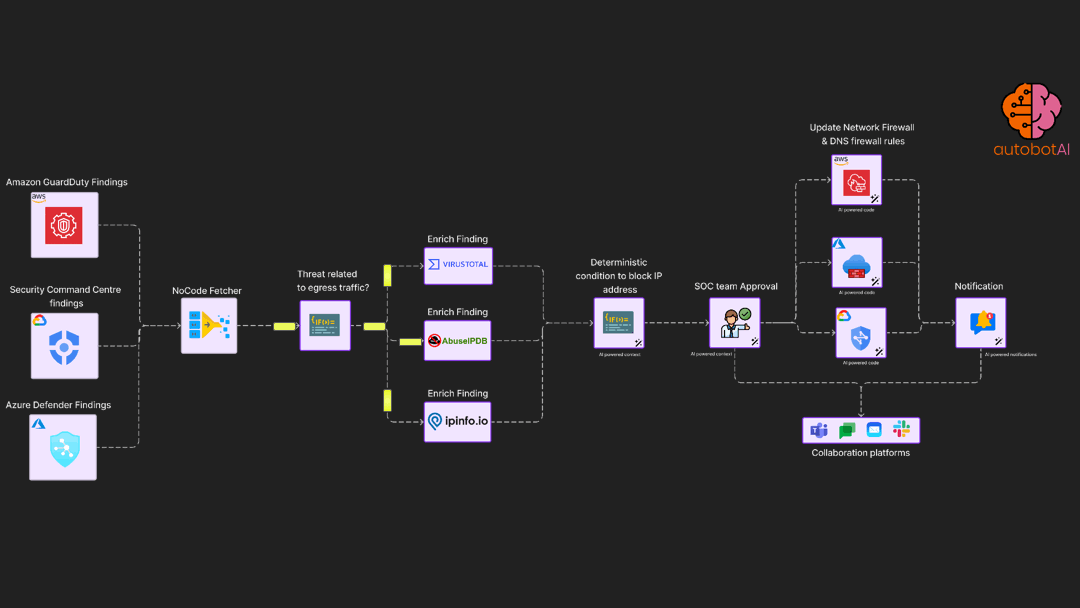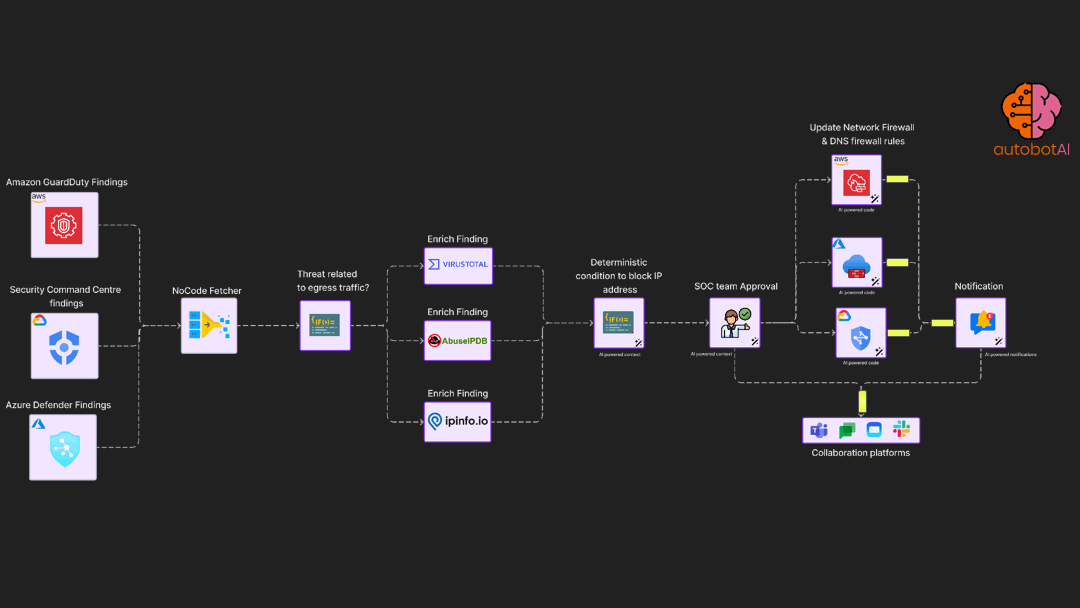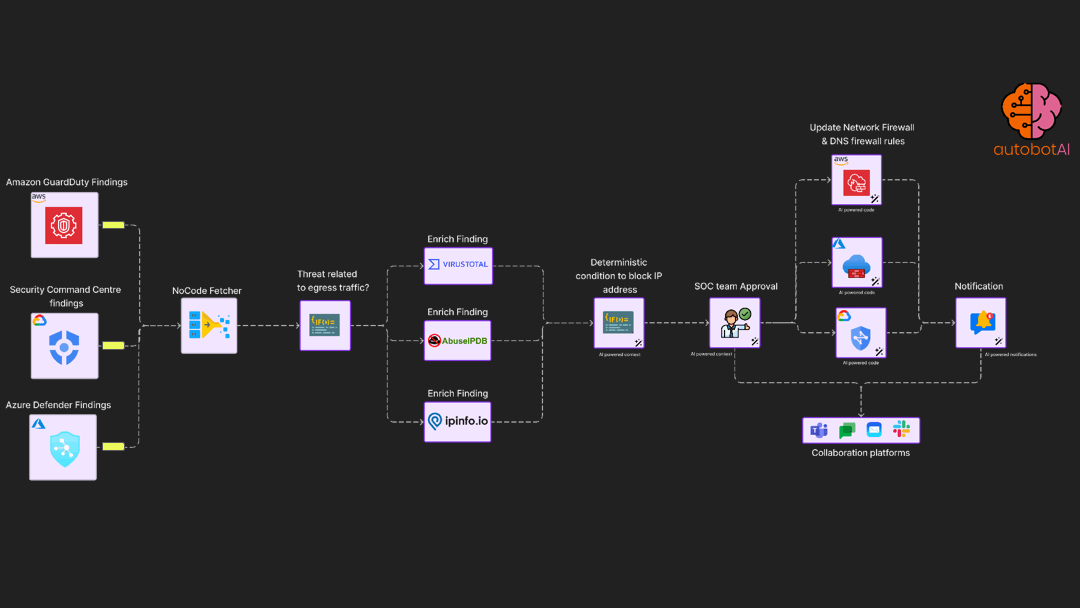
Operational excellence for availability
Automatically detect storage availability for cloud instance and cleanup or increase space based on user approval
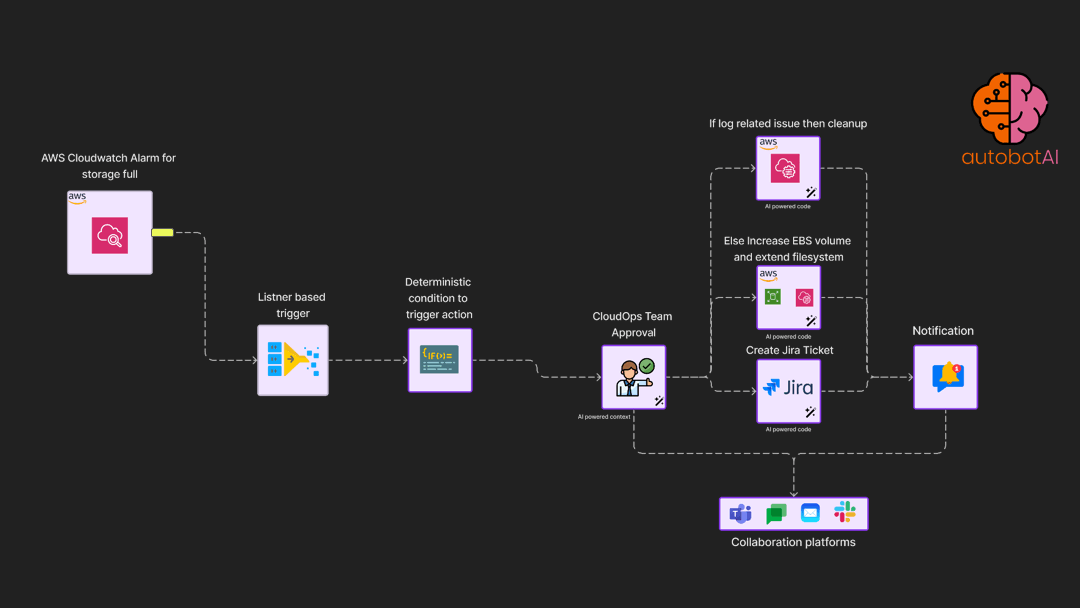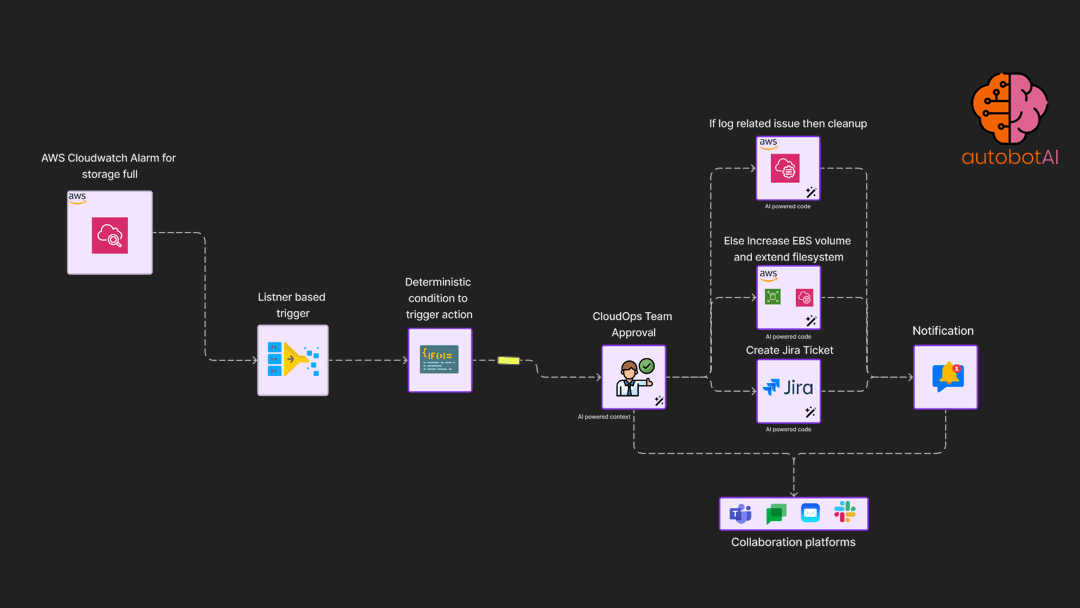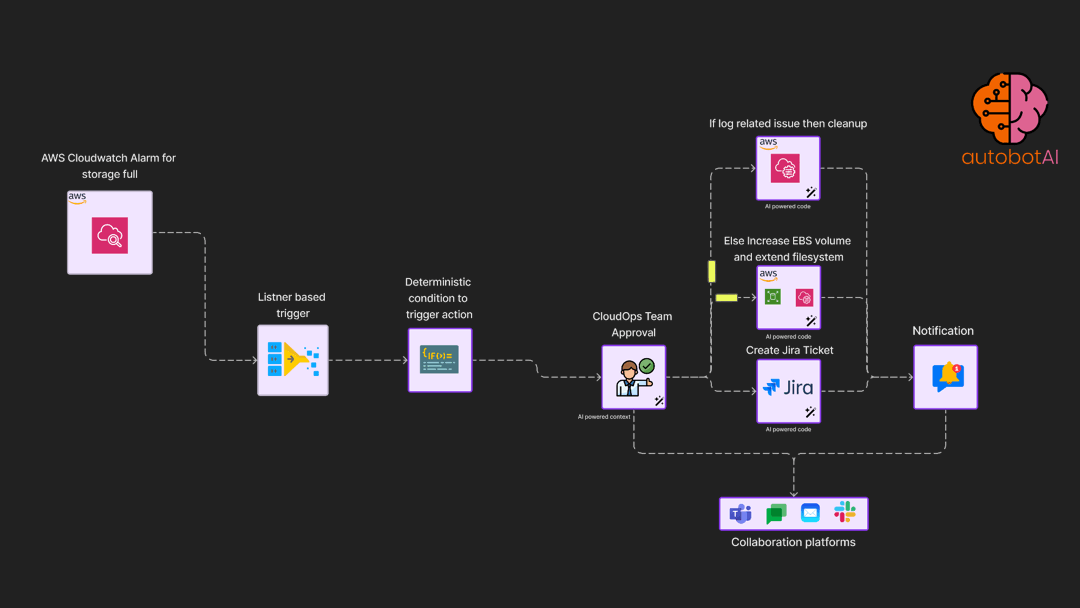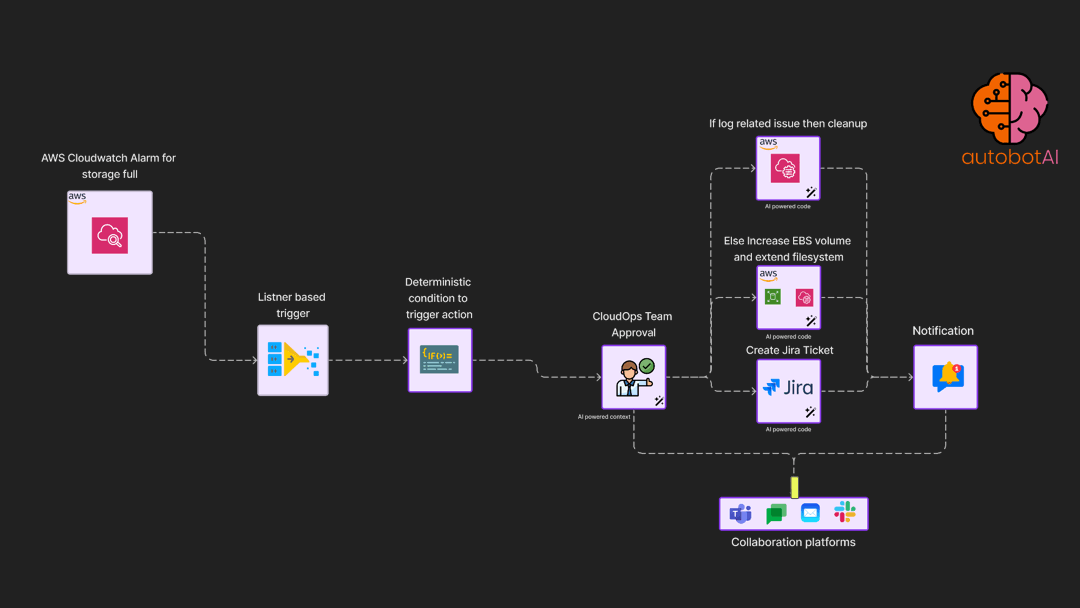
Results
Reduction of operational cost
30%
Improved MTTR by
60%
Reduced technical debt
48%
Adopting CloudOps and SecOps operations automation equips customers with the capability to significantly streamline their operational processes, leading to notable cost savings and enhanced efficiency. By automating the detection, troubleshooting, and remediation of application downtimes, organizations can reduce the need for manual intervention, allowing technical teams to focus on more strategic initiatives. This shift not only accelerates response and remediation times but also aids in systematically addressing and reducing technical debt. The automation of routine monitoring and problem-solving tasks ensures that issues are resolved swiftly and consistently, minimizing operational disruptions and contributing to a more stable, efficient IT environment.

Accelerate with automation experts
AutobotAI offers a unique approach to automation, providing it as a service where our dedicated team of automation experts meticulously crafts workflow solutions tailored to your specific needs.
autobotAI introduces a game-changing suite of integrations across security, cloud services, IAM capabilities, communication, ticketing, monitoring, and code repository management. By incorporating tools like Amazon Security Lake, Splunk, Google Directory, Microsoft Entra ID, Jira, Slack, Prometheus, Datadog, GitHub, and more, we're significantly enhancing the ability to streamline operations, fortify security, and ensure continuous compliance. These advanced integrations are designed to break down silos, providing teams with the means to achieve operational excellence and an enhanced security posture with unparalleled efficiency.
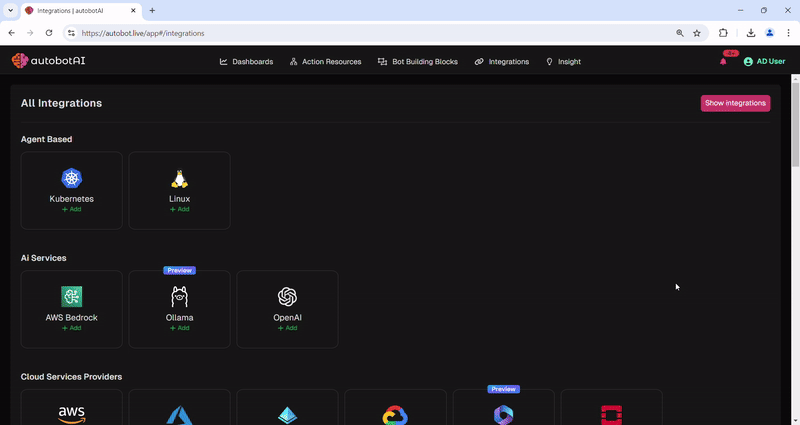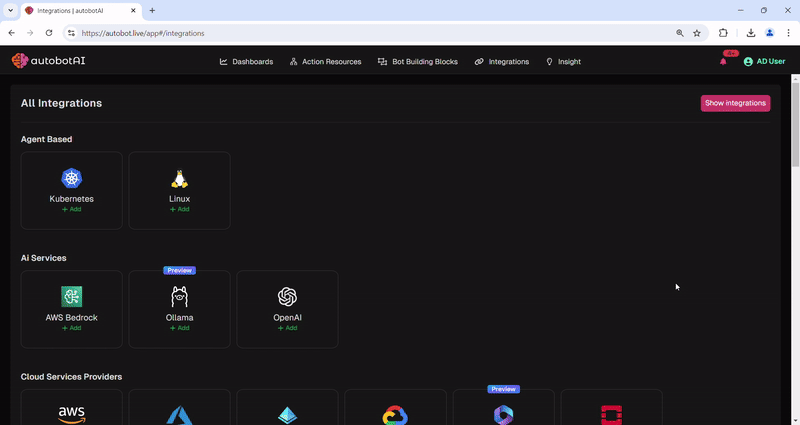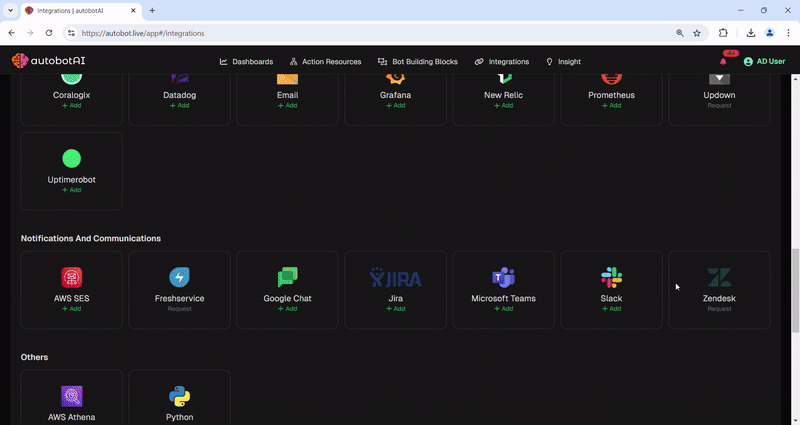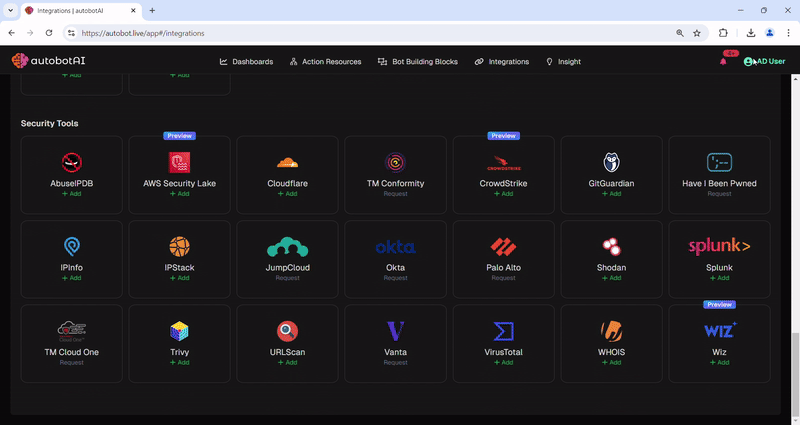
In today's fast-paced digital environment, achieving operational excellence through security automation is not just an option but a necessity. autobotAI is at the forefront of this transformative journey, offering a unique blend of expertise, technology, and support designed to help customers swiftly adopt and benefit from security automation. Here's how the autobotAI team facilitates a seamless adoption process and the advantages of partnering with us.
Personalized Consultation and Task Mining: The autobotAI team begins by working closely with customers to understand their unique challenges and requirements. Through a process of task mining, our experts identify repetitive, time-consuming tasks within your security operations that are ripe for automation. This initial step is crucial in pinpointing where automation can make the most significant impact, setting the stage for a tailored automation strategy.
Expert-Led Development and Implementation: Drawing on our deep domain expertise in security automation, the autobotAI team crafts customized automation workflows that align with your specific operational needs and security policies. Our approach ensures that automation is not just implemented but is strategically deployed to enhance security responsiveness and efficiency.
Advantages of Using autobotAI:
- Rapid Deployment: With autobotAI, businesses can fast-track the implementation of security automation, thanks to our ready-to-use integrations and pre-built templates. This rapid deployment capability allows you to quickly see the benefits of automation in action.
- Enhanced Security Posture: By automating routine security tasks, autobotAI not only frees up your security team's time but also reduces the risk of human error. Continuous monitoring, real-time threat detection, and automated remediation keep your digital assets protected around the clock.
- Operational Efficiency: autobotAI's security automation workflows are designed to optimize your security operations, streamlining processes and ensuring that resources are allocated effectively. This leads to a more agile and responsive security operation that can adapt to new threats and challenges as they arise.
- Scalability: As your business grows, so do your security needs. autobotAI's flexible platform scales with you, accommodating an expanding scope of security tasks and complexity without compromising performance or reliability.
- Insightful Analytics: With autobotAI, you gain access to actionable insights into your security operations. Our platform provides detailed analytics and reporting, helping you measure the effectiveness of your automation strategies and make data-driven decisions.
Taking the Next Step:
As you consider the next steps in adopting security automation, autobotAI invites you to reflect on the operational excellence of your current processes and resources. Are repetitive tasks consuming too much of your team's time? Could your security posture be stronger? If you see room for improvement, autobotAI is here to help you identify your automation use cases and guide you through the journey of transforming your security operations.
CONCLUSIONS
01 Identify Automation Opportunities
Begin with task mining to uncover and plan potential use cases for automation within your organization. This step sets the foundation for a targeted and impactful automation strategy.
02 Sign Up for autobotAI:
Configure your dedicated autobotAI workspace, integrating it with your existing tools and platforms. This centralized workspace serves as the launchpad for all your automation workflows.
03 Develop Workflows with AI Support:
Utilize autobotAI's generative AI capabilities to assist in creating effective automation workflows. This step harnesses the power of AI to simplify the workflow creation process, making it more intuitive and efficient.
04 Refine and Optimize Over Time
Measure operational excellance with custom dashboard and make adjustments as needed to align with evolving operational demands. This iterative process ensures sustained operational excellence and maximizes the benefits of hyperautomation
WHY autobotAI
Company
Certifications





© 2026 autobotAI. All rights reserved.
