Execute Terraform Configuration
Overview
The Execute Terraform Configuration action allows users to run Terraform commands directly in their bot workflows. This feature supports executing snippets of Terraform configurations, enabling efficient infrastructure management and automation. It facilitates the implementation of targeted changes related to security operations, such as adding security configurations or modifying resource settings, allowing for quick adjustments without the need for comprehensive deployment management.
Prerequisites
Linux Agent
- Agent Configuration:
Ensure the Linux Agent is configured. Refer to the Agent Installation Guide. - Ensure that the Terraform CLI is installed on the agent.
- Refer to the Terraform CLI installation guide for installation instructions.
- The cloud provider's configuration profile must be set in the agent configuration file, ensuring the necessary permissions to perform operations.
How to Use This Action?
To use the Execute Terraform Configuration action, follow these steps:
-
In your bot workflow, navigate to the Linux Actions and select Library.
-
Search for or locate the Execute Terraform Configuration action and drag it into your workflow.
-
Select the Linux integration that is connected to your Terraform-configured agent.
-
Under the Parameters section, specify the required parameter values according to your requirements. For more details, refer to the Parameter Details section.
-
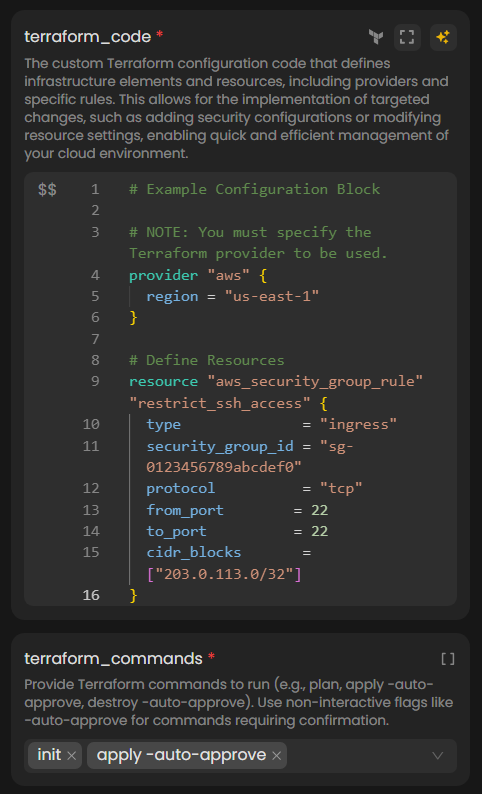
In the
terraform_codefield, you have two options:-
Manually Provide Code: Enter the Terraform code you want to execute. Ensure the code is in HCL (HashiCorp Configuration Language) and defines the provider, backend, and required resources.
-
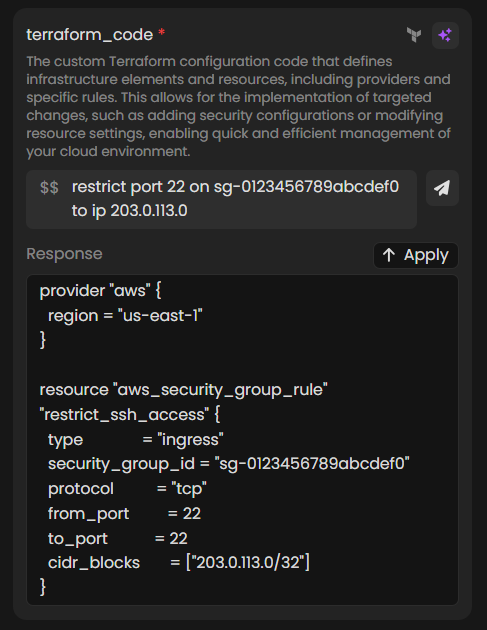
Use AI to Generate Code: Click the option to use AI assistance to automatically generate the Terraform code based on your specifications.
-
-
Specify the
terraform_commandsyou want to run, such asinit,plan, orapply. Be sure to include non-interactive flags like-auto-approvewhere applicable. -
Save or update the bot, then click on the Run button to execute the bot or the Run button inside the action node. Wait for the execution to complete. After execution, view the results in the execution details.
Parameter Details
| Parameter | Required | Description |
|---|---|---|
| terraform_code | Yes | The Terraform configuration code to execute. It must define the provider and required resources. You can either provide this code manually or use AI assistance to generate it. |
| terraform_code_directory | Yes | The directory path where the Terraform configuration will be saved. All directories are managed under ~/autobotAI-linux-agent/actions/terraform. |
| terraform_code_filename | Yes | The filename for the Terraform configuration file (defaults to main.tf). |
| terraform_commands | Yes | A list of Terraform commands to execute, such as init, plan, or apply. Provide non-interactive flags like -auto-approve where applicable. |
| run_as_user | Yes | Specifies the user under which the command runs (default value is "ubuntu"). If not provided, it will use root. Ensure Terraform is configured for this user. |
| config_profile | Yes | The name of the configuration profile for the cloud provider, e.g., aws/staging-account. Ensure that the necessary environment variables required by Terraform for the respective provider are set. For AWS, these include AWS_ACCESS_KEY_ID, AWS_SECRET_ACCESS_KEY, and AWS_DEFAULT_REGION. |
| execution_timeout | Yes | The maximum time (in seconds) allowed for command execution, (defaults to 900 ) seconds. |
Example Use Case
Scenario: Blocking a Malicious IP Address in a NACL
In response to an incident where GuardDuty identifies an instance as a target of an SSH brute-force attack from a malicious IP address, you can utilize this action to create a Network Access Control List (NACL) rule to block the IP across all ports. This proactive measure helps prevent unauthorized access, thereby enhancing your overall security posture.
Terraform Code to Create a NACL Rule: Example Terraform configuration to define and apply a new NACL rule:
hclprovider "aws" { region = "us-east-1" } resource "aws_network_acl" "example" { vpc_id = "vpc-12345678" ingress { rule_no = 100 protocol = "tcp" from_port = 0 to_port = 65535 cidr_block = "malicious.ip.address/32" rule_action = "deny" } egress { rule_no = 100 protocol = "-1" # All traffic from_port = 0 to_port = 0 cidr_block = "0.0.0.0/0" rule_action = "allow" } }
